Research Areas
- Error Correcting Codes for Streaming Communication and Computation
- Learning based Compression
- Privacy and
Security in Machine Learning
- Smart Meter Privacy in Electric Grids
- Secure MIMO Communication
Below we list a few topics that the research lab is actively pursuing with the relevant references.
Error Correcting Codes for Streaming Communications and ComputationApplications such as live-video streaming, web conferencing, and cloud computing are expected to see a dramatic growth over the next few years. Unlike classical systems, these applications require strict end-to-end delay constraints, real-time processing, and in-order delivery of data packets. Traditional error correction techniques are not designed for such constraints, and can lead to severe playback interruptions due to bursty packet losses over wireless channels.
Likewise many computation tasks used in applications such as machine learning are inherently sequential in nature. When designing error control codes in such applications one should account for the sequential/streaming nature of these applications. Our work has targeted the design of error control codes that account for such sequential applications.
References
- M. Nikhil Krishnan, Seyederfan Hosseini, Ashish Khisti, "Coded Sequential Matrix Multiplication For Straggler Mitigation" NeurIPS 2020
- M. Nikhil Krishnan, Erfan Hosseini, Ashish Khisti, "Coded Sequential Matrix Multiplication for Straggler Mitigation" IEEE J. Sel. Areas Inf. Theory 2(3): 830-844 (2021)
- M. Nikhil Krishnan, Erfan Hosseini, Ashish Khisti, "Sequential Gradient Coding for Packet-Loss Networks" IEEE J. Sel. Areas Inf. Theory 2(3): 919-930 (2021)
- Gustavo Kasper Facenda, Elad Domanovitz, Ashish Khisti,
Wai-Tian Tan, John G. Apostolopoulos,
Error-correcting codes for low latency streaming over multiple link relay networks, Submitted
- Elad Domanovitz, Silas L. Fong, Ashish Khisti, "An Explicit Rate-Optimal Streaming Code for Channels With Burst and Arbitrary Erasures" IEEE Trans. Inf. Theory 68(1): 47-65 (2022)
- Ahmed Badr, Ashish Khisti, Wai-Tian Tan, John G.
Apostolopoulos, "Perfecting
Protection for Interactive Multimedia: A survey of forward
errror correction for low-delay interactive applications".
IEEE Signal Process. Mag. 34(2): 95-113 (2017)
In recent years, deep learning methods are being increasingly used in both lossless and lossy data compression. Deep generative models when applied to (lossy) image compression tasks can reconstruct realistic looking outputs even at very low bit-rates, when traditional compression methods suffer from significant artifacts. Deep learning has also been applied in lossless compression tasks involving high dimensional data with intractable distributions, in techniques such as bits-back coding. Our recent work targets such applications
References
- H. Liu, G. Zhang, J. Chen and A. Khisti, "Lossy
Compression with Distribution Shift as Entropy Constrained
Optimal Transport", ICLR 2022
- G. Zhang, G. Qian, J. Chen and A. Khisti, " Universal Rate-Distortion-Perception Representations for Lossy Compression" NeurIPS 2021
- Daniel Severo*, James Townsend*, Ashish Khisti, Alireza
Makhzani, Karen Ullrich, "Compressing Multisets with Large
Alphabets" Data Compression Conference (DCC), 2022 Oral Presentation, An
earlier verison of this paper received a best paper award at the NeurIPS
workshops on Deep Generative Models for downstream
applications
- Elad Domanovitz, Daniel Severo, Ashish Khisti, Wei Yu, Data-driven Optimization for Zero-delay Lossy Source Coding with Side-Information, International Conference on Acoustics, Speech, & Signal Processing (ICASSP), 2022
- Daniel Severo, Elad Domanovitz, Ashish Khisti, "RCAQ:
Regularized Classification-Aware Quantization"
Biennial Symposium on Communications (BSC), 2021 - Yangjun Ruan, Karen Ullrich, Daniel Severo, James
Townsend, Ashish Khisti, Arnaud Doucet, Alireza Makhzani,
Chris J. Maddison, "Improving Lossless Compression Rates via
Monte Carlo Bits-Back Coding"
Long talk at International Conference on Machine Learning (ICML), 2021
Privacy and Security in Machine
Learning
As machine learning systems are being increasingly deployed in real world applications, there is a growing need to ensure safety, privacy and reliability of these systems. Our recent work is mainly focused on protecting privacy of data in a variety of scenarios during training and inference.
References
- Kuan-Chieh Wang, Yan Fu Ke Li, Ashish Khisti, Richard Zemel, Alireza Makhzani, Variational Model Inversion Attacks, NeurIPS 2021
- Erfan Hosseini, Ashish Khisti, "Secure Aggregation in Federated Learning via Multiparty Homomorphic Encryption". GLOBECOM (Workshops) 2021
- Tianrui Xiao, Ashish Khisti, "Maximal
Information Leakage based Privacy Preserving Data
Disclosure Mechanisms." CWIT 2019
Smart Meter Privacy in Electric Grids
Smart meters report real-time information of user's energy usage to utility providers. This can leak sensitiv information about the devices being used. For example see the figure below.
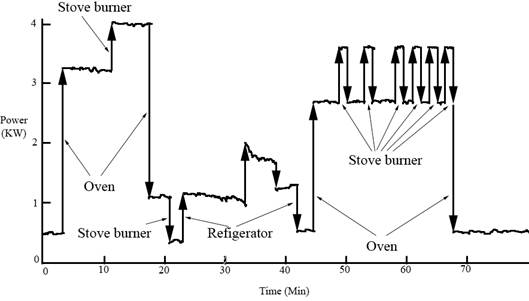
We consider the use of a rechargeable battery at user's home to mask information leaked to the utility providers. By determine the optimal charging and discharging policies of the rechargeable battery to mimimize information leakage.
References
S. Li, A. Khisti and A. Khisti, Information-Theoretic Privacy in Smart Metering Systems with a Rechargeable Battery
While multiple antennas have been
traditionally used in wireless systems to enhance
throughput and reliability at the physical layer, in
this project we examine their role in enhancing secrecy
against an external eavesdroppers.
When the transmitter uses a multiple
antenna array, it can exploit the directionality of the
channel vectors to create a strong signal gain at the
intended receiver, and a weak signal at other undesired
locations. It can achieve further improvement by sending
noise in the null-space of the intended receiver's channel.
This technique is called artificial noise transmission.
Consider the transmission of a confidential message to
a large number of legitimate receivers. In such a multicast
setup, we cannot use artificial noise transmission. This
is because when the number of receivers exceeds the number of
transmit antennas, we cannot find a null-space simultaneously
for all the channel vectors. We have developed a novel scheme
- artificial noise alignment, where we use an idea from the
interference alignment literature to align noise at the
legitimate receivers.
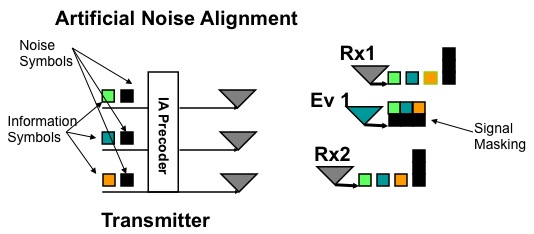
As shown in the above figure the multiantenna transmitter (with Nt antennas) transmits a superposition of noise and information symbols, such that:
- The noise symbols align at the intended receivers and only
require 1/Nt degrees of freedom
- The noise symbols occupy the full 1 degree of freedom at the eavesdroppers
- The information symbols occupy (1-1/Nt) degrees of
freedom, and can be decoded at the legitimate receivers.
- The information symbols are completely masked by the noise symbols at the eavesdroppers
The above scheme does not require the knowledge of the
eavesdropper's channel for noise alignment, just as in the
original artificial noise transmission scheme. For further
information, please refer to the following papers:
References
- A. Khisti, and D. Zhang, Artificial-Noise Alignment for Secure Multicast using Multiple Antennas IEEE Comm. Letters, Aug. 2013
- A. Khisti, Interference Alignment for the Multi-Antenna Compound Wiretap Channel IEEE. Trans. Inf. Theory, Special Issue on Interference Networks, March 2011
- A. Khisti and G. W. Wornell, Secure Transmission with Multiple Antennas-II: The MIMOME Wiretap Channel, IEEE. Trans. Inf. Theory, Vol. 56, No. 11, pp. 5515-5532, Nov. 2010
- A. Khisti and G. W. Wornell, Secure Transmission with Multiple Antennas-I: The MISOME Wiretap Channel, IEEE Trans. Inf. Theory, Vol. 56, No. 7, pp. 3088-3104, July 2011
